Wireless keyboard encryption cracked!
Written by IT News on 11:53 PM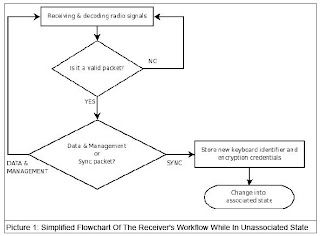
Wireless keyboards and mice are becoming an increasingly common sight on desks. However, wireless hardware carries large hidden risks. Dreamlab Technologies has shown that it is possible to capture and decrypt keystrokes, meaning that user names, passwords, bank details or confidential correspondence can be very easily eavesdropped.
According to this white paper, The two major consumer brands affected by this vulnerability are Microsoft and Logitec. In fact Microsoft’s Wireless Optical Desktop 1000 and Wireless Optical Desktop 2000 products are specifically mentioned as being vulnerable. It’s also assumed that other 27Mhz products such as the Wireless Optical Desktop 3000, 4000 and the Laser Desktop series are open to attack in a similar way.
Due to the widespread use of these wireless devices, the huge security implications and the fact that there is no quick fix for this design flaw (its take time to fix this bug); Dreamlab have decided not to release a public proof of concept.
It’s quite worrying to see just how easy it is to sniff and extract keystrokes from these ‘consumer’ grade devices with no need for dongles, trojans or specialist equipment. The 27Mhz keyboards only use 8bit encryption which can be cracked relatively quickly with quite modest hardware. From what I can tell all that’s required is a 27Mhz capable receiver, a sound card and a computer. The range will obviously be dictated by the receiver and its antenna.
Note: I'll still use wireless device for daily activity and my job, but not the commercial one.
 | Posted in »
| Posted in »




0 comments: Responses to “ Wireless keyboard encryption cracked! ”