Projekt V2: Crazy Computer Case Mod [PICS]
Written by IT News on 11:56 PMFrom concept to completion and nine months of labor, this is one pretty fantastic casemod.
read more | digg story
Provide comprehensive update related to Computer, technology, software, anti virus and another electric device
From concept to completion and nine months of labor, this is one pretty fantastic casemod.
read more | digg story
According to a keynote given at OSCON, Intel's PowerTOP application has allowed developers to get a close-up view of what is sucking power in a GNU/Linux system. Apparently they've gotten so much feedback and patches that they've been able to extend battery life by an hour since the first release, making GNU/Linux the best OS for power saving.
read more | digg story
 Last month we learned that some ISPs are inserting ads into web pages requested by their end users. Have you wondered how often this is happening, and whether it's happened to you? This web site is designed by the University of Washington and ICSI to answer these questions. Visit it to see if your ISP is modifying your web pages in flight!
Last month we learned that some ISPs are inserting ads into web pages requested by their end users. Have you wondered how often this is happening, and whether it's happened to you? This web site is designed by the University of Washington and ICSI to answer these questions. Visit it to see if your ISP is modifying your web pages in flight!
read more | digg story
 Ubuntu Feisty: 0$. Cardboard box: 0$. Duct tape: 1$. Having the bitchin'est case mod this side of the trailer park: priceless.
Ubuntu Feisty: 0$. Cardboard box: 0$. Duct tape: 1$. Having the bitchin'est case mod this side of the trailer park: priceless.
read more | digg story
Obrolanku: Memperkenalkan c-gold
c-gold.com ini lagi sedang memanfaatkan moment atau beneran bisnis ya? atau jangan-jangan hanya HOAX?
Abisnya web dan systemnya copy paste dari e-gold, mirip banget.
Thanks to Jimmy Ruska’s video on YouTube, there are several quirks about phrasing search queries for Google that can find you files in a jiffy. I will detail the method and include it as a Firefox bookmark first, and then I’ll follow up with detailed information on the actual query.
Adding a bookmark
Here’s the process to have a bookmark in Firefox such that you can search for an MP3 song in Google by just typing “music yourSongTitle” in the Firefox address bar.
1. Create a new bookmark
2. Fill in the following for the fields in the window that appears
“http://www.google.co.in/search?hl=en&q=intitle%3A%22index.of%22
+%28mp3%29+%s+-html+-htm+-php+-jsp&btnG=Google+Search&meta=“
(Include the whole query, without the quotation marks)
3. Now open a new tab and type “music yourSongTitle” and viola! — you will see links of directory listing for the MP3 you wanted
Deciphering the query
The crux of this hack is the clever usage of Google search tags for narrowing the result to only directory listings with keywords “MP3″ and negating results that include html, htm, php or jsp as directory listings.
Here is the break up of the query and the meaning of the tags:
You can modify the same query for searching pdfs or any other file format. Also, there are few more keywords to limit the search to a particular site (site:siteName) or a filetype(filetype:pdf). I am no promoter of media piracy and the use of Google tag words makes search all the more effective and productive for daily use. Jimmy has also uploaded a new video on the implementation with few more features on his own site.
Nokia’s acquisition of social media sharing website Twango, marks another milestone in the handset majors move to capitalize on the proliferation of media on the web. Already, the N series phones have been branded as Multimedia PCs. This latest move provides more impetus to on the move anytime, anywhere computing.

A quote from the article at Tech.co.uk
“The Twango acquisition is a concrete step towards our Internet services vision of providing seamless access to information, entertainment, and social networks - at anytime, anywhere, from any connected device, in any way that you choose,” commented Anssi Vanjoki, Executive Vice President and General Manager, Multimedia, Nokia.
The move puts more options in the hands of people to share and manage videos, music and documents. Twango is a Washington; Redmond based start-up, founded by ex-Microsofites.
More sources:
Nokia buys media sharing site Twango (News.com)
Nokia announces acquisition of Twango (Pocket-lint)
These are indeed testing times for companies deeply associated with Telecom. Computer firms have been steadily encroaching into erstwhile telecoms space (Google planning to bid for spectrum, Apple launching the iPhone)Obrolanku: Mengatasi Cacar air
Cacar air adalah adalah salah satu penyakit umum yang pernah dimitoskan sebaga salah satu penyakit yang pasti dilewati oleh anak-anak, bisakah dicegah?
Obrolanku: Periksa keamanan komputer dengan ProcessScanner
Tools ini mirip dengan processexplorer, namun ini online
Apa sih "morning sickness" apa iya ada kaitanya dengan kanker payudara? Jika anda seorang perempuan, tentu saja judul artikel ini sering terlintas dibenak anda bukan? Jangan kawatir, berdasarkan sumber yang bisa dipercaya dari sebuah pertemuan bertema "The Society for Epidemiologic Research" yang telah meneliti lebih dari 1.001 perempuan telah..
read more | digg story
Yahoo describes Pipes as “an interactive data aggregator and manipulator that lets you mashup your favorite online data sources”. But what does that mean to the rest of us? This tutorial will take you through the steps to filter the content of one RSS feed (Techmeme) so that content you may have already read isn’t included in your Techmeme feed.
read more | digg story
Two hours of sleep a day is plenty.
read more | digg story
Here are 10 habits you should set aside right away to free yourself from the many problems each one will be causing you.
read more | digg story
Zero Install is a way to run software without an explicit installation step. This is easier (install and run becomes just run) and safer (installation doesn't happen as root).
read more | digg story
To simplify access to the tools in Windows XP’s Control Panel, Microsoft created the Category View, in which the Control Panel’s tools are organized into categories. If you’re an old-school Windows user, you can still switch back to the Classic View, in which all of the Control Panel’s tools are available. If you admire the simplicity of the Category View but prefer the Classic View, you may want to create your own custom Control Panel that combines the best of both views. Here’s how:
Virus: Worm/Zafi.B
Date discovered: 11/06/2004
Type: Worm
In the wild: Yes
Reported Infections: High
Distribution Potential: Medium to high
Damage Potential: Medium
Static file: No
File size: 12.800 Bytes
Methods of propagation:
• Email • Peer to Peer
Aliases:
• Symantec: W32.Erkez.B@mm • Mcafee: W32/Zafi.b@MM • Kaspersky: Email-Worm.Win32.Zafi.b • TrendMicro: PE_ZAFI.B • F-Secure: Email-Worm.Win32.Zafi.b • Sophos: W32/Zafi-B • Panda: W32/Zafi.B.worm • Grisoft: I-Worm/Zafi.B • VirusBuster: I-Worm.Zafi.B • Eset: Win32/Zafi.B • Bitdefender: Win32.Zafi.B@mm
Platforms / OS:
• Windows 95 • Windows 98 • Windows 98 SE • Windows NT • Windows ME • Windows 2000 • Windows XP • Windows 2003
Side effects:
• Uses its own Email engine • Lowers security settings • Registry modification
I recommend to always update your virus data files
if you don't have any anti virus installed in your computer, go here
Sober.X - HIGH RISK Virus Alert
First Report About This Virus:2005-11-19 18:34
Sober.X - MEDIUM RISK Virus Alert
First Report About This Virus:2005-11-19 18:34
Sober.P - MEDIUM RISK Virus Alert
First Report About This Virus:2005-10-06 06:12
Sober.r - MEDIUM RISK Virus Alert
First Report About This Virus:2005-10-06 03:47
RBOT.CBQ - MEDIUM RISK Virus Alert
First Report About This Virus:2005-08-16 23:46
RBOT.CBQ - MEDIUM RISK Virus Alert
First Report About This Virus:2005-08-16 23:46
IRCBot.es - MEDIUM RISK Virus Alert
First Report About This Virus:2005-08-15 18:55
MiniDl-A - MEDIUM RISK Virus Alert
First Report About This Virus:2005-06-03 04:37
BOBAX.P - MEDIUM RISK Virus Alert
First Report About This Virus:2005-06-03 00:26
Mytob.bh - MEDIUM RISK Virus Alert
First Report About This Virus:2005-05-29 22:52
SUSE has issued an update for php4 and php5. This fixes some vulnerabilities, where one has an unknown impact and others can be exploited by malicious, local users to bypass certain security restrictions and gain escalated privileges, and by malicious people to to cause a DoS (Denial of Service), bypass certain security restrictions, and potentially compromise a vulnerable system.For more information:
Solution:Apply updated packages.
Some vulnerabilities have been reported in Apple QuickTime, which can be exploited by malicious people to compromise a user's system.
click here to continue reading this article
Intel said Friday it will join the board of the One Laptop Per Child program and contribute funding to the project which created and is distributing the XO computers for education. This comes after Intel execs have been critical of the design, and after they designed and promoted a competing child-focused portable, their $225 Classmate PC, a more conventional machine than the radically rethought XO boxen.
Various sources have recently priced the simple Linux portables at $150-$175 each as a result of hardware upgrades, although the program recently said costs should reach the $100 goal soon, and drop further in short order thereafter. Those would make a dandy e-book reader, and put further price pressure on Sony’s e-book readers.
The XO machines now use AMD CPUs. AMD reps said “Intel’s apparent change of heart is welcome, and we’re sure they can make a positive contribution to this very worthy project for the benefit of children all over the world.”
A virus scan that I use blows what sounds like a foghorn when it’s done. I try to be out of the room because it’s so loud and annoying. I prefer a gentler approach. Blinking signs are a good attention-getter, without being harsh.
There are two ways to blink a control or text: on and off or by switching colors. Of course, blinking text won’t replace a sound cue, but done well, it’s easy on the eyes and nerves.To blink on and off, use a Timer event in the following form:
Private Sub Form_Timer()
Me!control.Visible = Not Me!control.Visible
End Sub
Each time the form executes its timer event, this code toggles the control’s Visible property. You can use this simple technique to blink just about any control, but the control can’t have focus at the time.
Switching between two colors is just as easy:
Private Sub Form_Timer()
With Me!control
.ForeColor = IIf(.ForeColor) = color1, color2, color1)
End With
End Sub
The form’s timer event alternates between color1 and color2. Use integer values or constants for colors. For instance, use 0 or vbBlack for black, and 255 or vbRed for red. This probably works best with a label or command button, but you could use it with any control that has a Fore Color property.
Blinking text doesn’t necessary mean the user has to do anything, but it can. How the user reacts to the text is really up to you. In both of these simple events, the blinking is continuous; it won’t stop when the user takes some action.
If the control or text fails to blink, check the form’s Timer Interval property. A setting of 500 creates a reasonable blink. A setting of 50 is so fast that it creates a neon effect. This works only with forms, as reports don’t have a Timer event.
Private Sub Form_Timer()
Me!control.Visible = Not Me.control.visible
End Sub
Few communications tools give you as much exposure as e-mail. Unfortunately, mistakes in your e-mail will receive that same exposure. Calvin Sun cites 10 common e-mail habits and missteps that annoy him (and maybe you as well) and explains what you can do differently.
click here to continue reading this article
There has been a lot of talk about Facebook unseating MySpace as the top social network. While that may (or may not) happen sometime in the future, the so-called gray lady of Social Networks is holding its own.
read more | digg story
Researchers have found a way to record to nanostructures in DVD-sized discs to store 500GB of data, and the team says that it will eventually be able to store 1 terabyte of data on those same discs with high data throughput rates.
read more | digg story
According to Microsoft, the Live Earth concerts were the most watched event in online history. That's pretty impressive for an event that was the least watched television show last Saturday night.
read more | digg story
The Open Internet Coalition is on Capitol Hill to talk about anti-competitive practices in the wireless industry and pitch the need for device portability across carriers, sane termination fees, and smarter management of new spectrum.
read more | digg story
All the development going on with the free Nouveau has paid off. Today the free driver has outperformed the existing nv driver by 64%. The GtkPerf benchmark was used.
read more | digg story
The BitLord show released a special episode in which they interview with Brokep from The Pirate Bay. Brokep talks about TPB’s contribution to the BitTorrent scene, their secret upcoming project, the new anonymous P2P protocol they are working on and much more.
read more | digg story
Neuros' hacker-friendly set-top-box can now browse, search and view YouTube -- thanks to the efforts of the open-source community.
read more | digg story
Our iPhone review is rather large because we unleashed three (and a half) reviewers on it, all coming from different backgrounds. We pooled our thoughts together, had a few fistfights and a squabble or two ("Keyboard sucks!" "Does not!"), and now present to you our full review. Check out the outline beforehand, or just jump on in.
read more | digg story
Converting a PPT to a PDF is like turning meat, veggies, spices and water into stew. Pretty simple.
But adding pdf file into power point is not easy as other files such JPG, GIF and other graphic file format. Some users in my office don't know how to do this.
It's not likely that anybody can do a very good job of it, but it's worth checking the current crop of PDF tools at places like Planet PDF and PDFZone
But .... You can import PDF content into PowerPoint in several ways, depending on what software you have and the result you're after.
The simples way is by using Insert object, while the user only familier with Insert picture from file.
Here is the step:
 Remember, this is an embeded object, when double clicked the object it will automatically open your pdf viewer.
Remember, this is an embeded object, when double clicked the object it will automatically open your pdf viewer. Some time ago I saw a chocolate bar made with Adobe Photoshop somewhere on the Internet. I thought that Gimp can
’t do worse than and I got myself to work. It seemed to be quite easy and here is the result in 28 steps.

 As you may know, both yahoo and google offer free services for webmail. Gmail is the first offering large amount of mailbox capasity folowed by yahoo. Yahoo is now offer a higher storage capacity (unlimited storage, compared to its previous 1000MB).
As you may know, both yahoo and google offer free services for webmail. Gmail is the first offering large amount of mailbox capasity folowed by yahoo. Yahoo is now offer a higher storage capacity (unlimited storage, compared to its previous 1000MB). Gmail offers 1GB (1000MB) of storage. But is not easy to register if you are common user and don't have enough knowledge on proxy. Right now, Gmail is only available to people who are invited by other existing Gmail users.
Gmail offers 1GB (1000MB) of storage. But is not easy to register if you are common user and don't have enough knowledge on proxy. Right now, Gmail is only available to people who are invited by other existing Gmail users.
I’ve been a long time using Yahoo Mail. Ever since I shut my plasa.com account some years ago, and left all my other free email accounts, I’ve been loyal to Yahoo Mail. I found an auction for Gmail invitation on eBay, I suggest you don't need to pay for free mail service, yahoo is now offring unlimited size of storage.
I need your comment regarding this issue, which one is realy good to have?
 |
 Intel is very fast on upgrading their technology on processor. It seem just yesterday they launched the core 2 duo processor, now they have Intel vpro processor.
Intel is very fast on upgrading their technology on processor. It seem just yesterday they launched the core 2 duo processor, now they have Intel vpro processor.code:EAX1050/TD/256M
ASUS VGA EAX1050 TD 256M RADEON X1050 PCIE 256M(EFFECTIVE MEMORY UP TO 1GB)
Outstanding Gaming Experience:
Supports today's top game titles and combines smooth gaming performance with stunning 3D image quality Superior Visual Output.
Compare price at http://www.shopbot.ca/p-46180.html
According on my first used of Google spreadsheet and documents (beta version) it is clever idea, google know wht people looking for. It's easy to use, fast enough for web based 
If you always connected to the internet to help you find something or for your work, or for just browsing, it's highly recommend to always activate your firewall, especialy if you running windows XP and don't third-party firewall software.
And if you don't know what is firewall, firewall is a hardware or software device which is configured to permit, deny or proxy data through a computer network which has different levels of trust, in other case i can say that firewall is your god for security. And windows xp SP2 already built in standard firewall.
Windows Firewall, previously known as Internet Connection Firewall or ICF, is a protective boundary that monitors and restricts information that travels between your computer and a network or the Internet. This provides a line of defense against someone who might try to access your computer from outside the Windows Firewall without your permission.
If you're running Windows XP Service Pack 2 (SP2), Windows Firewall is turned on by default. However, some computer manufacturers and network administrators might turn it off. But please do not turm it off for any reasons.
To open Windows Firewall
 | |
After got a new Solidedge 3D licensed software, I think that I need new PC with high speed and performance. The candidate should be able to handle the 3D aplication and graphic design such SolidEdge 3D. The old hardware seem to be very slowly, coz it's Intel Pentium 4, 1.8Ghz.
Spending about $600.00 for this new assembled PC (assembled by myslef)
I decide to use ASUS P5L2D2 SE/C, support Intel core 2 DUO, and support Intel Next generation 04B/04A and 05B/05A cpu.
And the processor is Intel core Duo, e4300*, 1.8Ghz, 800Mhz, 2MB L2 Cache.
And the PCI express is Asus EAX1050, 256MB, chipset by ATI.
And the memory is VISIPRO DDR-2, 2 x 1GB
And the Hard disk is 320GB, 7200rpm by Seagate
The OS is Microsoft windows XP pro (event the hardware support vista already)
wooow, coool, great.. this is the fastest machine I have ever, running SolidEdge 3D better then before. It is worthy to have this new PC with only spend $600.00, already include Samsung LCD, 17", DVD-RW by LiteON, Casing by Simbada SimCool, keyboard and mouse by Logitech.
There are several ways you can determine your local IP address information:
IPCONFIG
This will opens a command window. One advantage is that you can send the information to a text file
(IPCONFIG /ALL > c:\ip.txt)
But sometimes the window shows show much information you need to scroll around to find it.
VIEW STATUS

What is Virtual Memory? and what is the page file? In any windows disk partition by default will exist page file, some times the file is bigger day after day. So, what is the page file for? can we delete or just not activate it? Here you will lear a litle bit about virtual memory and how to clear it when windows shuting down.
Virtual memory is a program instruction on an Intel 386 or later CPU can address up to 4GB of memory, using its full 32 bits. This is normally far more than the RAM of the machine. (The 32nd exponent of 2 is exactly 4,294,967,296, or 4 GB. 32 binary digits allow the representation of 4,294,967,296 numbers — counting 0.)
The page file in XP is a hidden file called pagefile.sys. It is regenerated at each boot — there is no need to include it in a backup.
To see it you need to have Folder Options | View set to ‘Show Hidden and System files’, and not to ‘Hide Protected mode System files’. Just if you feel need to clear the cache or page file size, here is to do that on shuting down:

If you are running windows XP or higher version, by default the first installation will suggest you to choose NTFS file system format. If by accident your file system format is Fat or Fat32, you still able to convert into NTFS file system, here is how:


Many ways to get into System properties such as goto control panel and double click System icon or by right clicking on my computer folder within explorer.
Here I saw you the shortest way to get the system properties:

Just yesterday, got mail from my client, requesting some tips on how to disable the windows automatic update. I'm asking to him "why should you disable the automatic update?" I told him that it's not recommended to disable it windows automatic update, event its posible to do that.
The most probably reason is because he don't have product license, well i don't care about the reason. I decide to help him.
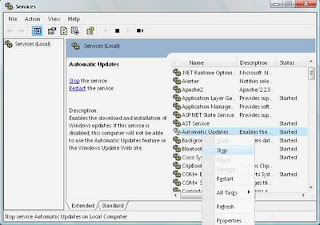
It turns out to be pretty easy. Courtesy of Coding Horror are two ways: you can either use the command line to shut off the Automatic Updates service or manually shut it off in the Services panel.
To shut it off manually:
It looks like Intel is working on an anti-cheat technology, although this is only a research project at the moment and hardly ready for prime time.
The concept is simple: A chipset records all input from the keyboard and mouse at the hardware level — the game also does the same. If the two doesn’t match, then something else is pumping input into the game, and you are probably ‘cheating.’
The general idea here is that, if something tampers with input, it should be flagged. Obviously, the game will first have to support the chipset, as it will have to be the one querying the hardware in order to compare the various input streams.
You can read more about Intel’s anti-cheat technology in The Inquirer.
Personally, I can immediately see some potential issues with this setup. One main problem would be with hardware or software that reads or writes to the keyboard or mouse queue. I wrote a hotkey plug-in for Winamp a few years ago (Winamp KeyControl), and I can just see how this anti-cheat implementation will scream murder at every other key press.
Additionally, I am pretty sure it will be hacked very quickly when released anyway.
Anything to say on the current state of cheating in online games? Join the discussion, or get back to your work!
If you have a secure folder on your server, you may want to avoid using DSN because it's a little bit slower. I've set my data folder to be "secure". This means, the folder has full permissions for the asp engine context, but no permissions for the visitors.
Let's create the connection and recodset objects now.
<%
set conn = Server.CreateObject("ADODB.Connection")
set rs = Server.CreateObject("ADODB.Recordset")
%>
First way to define where your database is to use relative location by utilizing Server.MapPath method.
<%
'Define the location of your database
'as follows if you want to use a relative folder.
cDBLocation = "/securedata/mydatabase.mdb"
'Construct the connection string using MapPath.
sConnSample = "Provider=Microsoft.Jet.OLEDB.4.0;" & _
"Persist Security Info=False;Data Source=" & _
Server.MapPath(cDBLocation)
%>
You may want to define your physical database location. You should always use the physical location if you can.
<%
'If you are sure about the pyhsical location
'of your database, it's better to use it that way.
cDBLocation = "c:\securedata\mydatabase.mdb"
sConnSample = "Provider=Microsoft.Jet.OLEDB.4.0;" & _
"Persist Security Info=False;Data Source=" & _
cDBLocation
%>
After defining the location, it's time to connect to the database and get the records!
As a sample, I've defined two re-usable functions for opening and closing the connections. Of course, there are much better ways depending on the functional needs of your application, but you can still use the following code.
<%
'ADO Constants
Const adOpenForwardOnly = 0
Const adOpenStatic = 3
Const adCmdTable = 2
sub OpenDB(sConn)
'Opens the given connection
'and attachs the recordset to it
conn.open sConn
set rs.ActiveConnection = conn
'Using a static cursor, you will be able
'to use AddNew and Update methods.
'Consider using adOpenForwardOnly if you
'are only reading records (much faster).
rs.CursorType = adOpenStatic
end sub
sub CloseDB()
'Closes the active connection
'And cleans up the memory
rs.close
conn.close
set rs = nothing
set conn = nothing
end sub
%>
You may execute an SQL statement to get your recordset filled:
<%
OpenDB sConnSample
sSQL = "SELECT Field1, Field2 FROM TestTable"
rs.Open sSQL,,, adCmdTable
'Display the records anyway you want
CloseDB
%>
I hope this sample gives you a quick overview of connecting to Access Mdb files.
You are always welcome to express your feedback!
After 13 years as the world's richest person, Bill Gates appears to have been dethroned. But there will probably be no sobbing inside his Medina estate.

In his own words:
Bill Gates on the pitfalls of being the world's richest man:
In fact, based on his past remarks, the Microsoft Corp. chairman might welcome the news.
Mexican telecommunications tycoon Carlos Slim has taken the crown with a net worth of $67.8 billion, according to estimates by a respected financial news site in Mexico, as reported by multiple news services.
The main reason: a 27 percent surge in the stock price of Slim's wireless company, America Movil, in the second quarter.
At a Microsoft conference in Redmond last year, advertising executive and TV host Donny Deutsch asked Gates if he would be upset if someday he were no longer the world's richest man.
"I wish I wasn't," Gates replied. "There's nothing good that comes out of that."
"It's better than being second," Deutsch said.
"No," Gates replied. "You get more visibility as a result of it."
Slim's new standing might not be considered official until the next publication of Forbes' ranking of the world's richest people.
On this spring's Forbes list, Slim was just behind investor Warren Buffett, the chief executive of Berkshire Hathaway, who had been second on the list for years.
In April, after the publication of the official 2007 list, Forbes reported that Slim had surpassed Buffett to become the world's second-richest man. At the time, Forbes reported that Slim was "breathtakingly close" to passing Gates for the No. 1 spot. Gates' estimated worth was $56 billion at the time.
For the latest estimate of Slim's worth, Reuters quoted financial tracker Eduardo Garcia, from Sentido Comun, an online financial publication in Mexico. Garcia estimates that Gates is currently worth $59.2 billion.
According to an Associated Press report from Mexico City, Garcia's estimate of Gates' wealth was based on a 5.7 percent increase in Microsoft shares in the second quarter, and doesn't include Gates' sizable holdings apart from Microsoft shares.
"But a 26 percent growth rate for a world company like America Movil, that's hard to top for one quarter," Garcia said, according to the AP report.
Gates has put a total of more than $30 billion into the Bill & Melinda Gates Foundation, reducing his personal net worth. Slim recently told The New York Times that he plans to boost the endowments of his companies' foundations to $10 billion in the next four years, from the current total of $4 billion.
Slim, meanwhile, seems just about as interested in holding the "world's richest" title as Gates was. The AP quoted Slim's spokesman as saying, "As he has said many times himself, he is not in any competition."
FeedBurner has ceased charging for two premium features following their acquisition by Google in May.
FeedBurner Stats PRO, a service that provides detailed statistics including subscriber numbers, item clickthrough tracking, podcast downloads and aggregate item uses amongst other features, becomes free.
FeedBurner MyBrand, a service that allows users to control the URL of feeds is now free as well; a move that will be strongly welcomed. For many, the biggest argument against using Feedburner was the need to give up control of your feed URL (for example, http://feeds.feedburner.com/Techcrunch ). Being able to keep ownership of a feed complete with site branding will drive new many new users to Feedburner, including yours truly.
). Being able to keep ownership of a feed complete with site branding will drive new many new users to Feedburner, including yours truly.
FeedBurner PRO and MyBrand accounts will not be billed effective from June. Although the services are now free, Feedburner users are required to “upgrade” to them from within the Feedburner control panel.
Worried about sensitive data in your Microsoft Word document? you can both encrypt and password protect the document to keep it secure. This feature is very useful if you have to store your documents in a shared location, such as a network folder or home computer.
To encrypt your document, click on the Microsoft Office Button in the upper left hand corner, select Prepare from the left-hand menu and then choose Encrypt Document.

In the Encrypt Document dialog window type in your password for this document.

You will then need to enter in your password again for verification and click OK. You will not receive any type of confirmation message, this window will simply disappear.

By default Word 2007 will save your document with 128-bit advanced encryption. Now when anyone goes to open the document it will automatically ask for the password.

That's all there is to it.
Another feature that i love from Office 2007 is it ability and easy to rotate any objects such picture. When you are including graphics in a Word document many times you want to place the image in a particular way or at a certain angle. Word 2007 has just the tool for the job.
Open your Word document and click on the picture or graphic you want to move. You will see the edit outline around your graphic. Now left click the top green knob and hold the object and start to rotate it.

Below you can see the graphic start to move.

In the second picture here I added an object and am rotating it as you will notice the first graphic is at an angle.

Here is the result of a couple of simple objects in a Word 2007 document that I rotated around a bit so you have an idea.

You can do this with any picture, graphic, and even text!
Do you wish the IE7 Menu bar was located where it was in IE6? Here is how to quickly create a registry fix to move it back to the top.
After you install IE7 you have to make the menu bar appear. Right click an empty spot on the tool bar and place a checkmark next to Menu Bar. It will also show up temporarily if you hold down the Alt key.

You will see that IE 7 puts the Menu Bar underneath the Address Bar which we don't want.
Open up notepad by clicking Start \ Run, type in notepad and click OK.

Copy and paste the following script into notepad. You do not need to modify the code at all. Just copy and paste it into notepad.
REGEDIT4
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\]
"ITBar7Position"=dword:00000001
Here is how we turn it into a reg key fix. Click on File \ Save As, but don't click on Save until you read the next step.

Change your notepad Save as type to "All Files" and name the file something like IE7_Toolbar_fix.reg. Naming the file with the .reg extension is the key for this to work. Now you can click on Save.

You have just created a registry fix! Now double click the file you just created.
You will get the following confirmation screen. Click Yes.

The next screen will be confirming the registry key was added.

Close out of Internet Explorer if it is open and relaunch it. The Menu Bar is now on top!
Uninstall
To change the Menu bar back to the original position, use this registry script instead:
REGEDIT4
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\]
"ITBar7Position"=dword:00000000
Residents of Maryland were recently challenged by their governor to cut their energy consumption by 15% over the next eight years as he pledged to reduce the use of energy by government offices and to increase the energy efficiency of government buildings. This and other energy conservation projects (a quick Google search revealed similar calls in several states) are poised to become large movements, particularly as energy costs balloon as a result of rising oil prices.
State residents challenged on energy savings (Baltimore Sun)
IT shops will be forced to respond to mounting energy costs. Dell has already announced an initiative to cut energy consumption by its servers by 42% while delivering the same or higher performance. Gartner has posited that nine to fifteen percent of most businesses’ energy costs are related to IT, the vast majority from desktop PCs, and suggests “more-aggressive power management” for businesses. HP has also caught the conservation bug, planning to reduce energy usage by 15% over the next three years by using advanced techniques for powering and cooling data centers.
Dell-Emerson Partner to Reduce Power Consumption in Customers’ Data Centers by 42 Percent (WebWire)
Switch off your PCs to cut costs and help the environment (Moneyweb)
Averting the IT Energy Crunch (BusinessWeek)
My organization has already started to reduce energy consumption by closing on Fridays during the summer to save on cooling costs during the hottest months of the year. We have also been asked to look into power management options to reduce PC power consumption.
Using a variety of nefarious methods, phishing and pharming are a consistent problem that threatens everyone with identity theft. If you recognize what these methods are and how malicious users employ them, you can keep yourself and your users from becoming a victim.
Phishing involves sending an e-mail that claims to be a legitimate business in an attempt to scam the user into surrendering private information. Pharming involves the same goals with a different method; malicious users employ spyware, keyloggers, domain spoofing, domain hijacking, or domain cache poisoning to obtain personal or private (usually financial) information.
To put it bluntly, criminals try to steal your identity by getting you to divulge financial data such as credit card numbers, account usernames, passwords, and social security numbers. They sell this information, and it then becomes an identity theft crime.
The primary method for this crime is to send e-mails that look like valid correspondence coming from a bank asking users to click the link provided and log into their account for some type of important information. But your bank and other institutions where you do business don’t work this way. They may send you an e-mail and ask you to review or verify information. However, they don’t send links to a Web site. You already do business with them, and they know you don’t need the link to the Web site.
If you click that link, one of two things is going to occur. It could download spyware onto your computer, which will then capture your personal information and send it to the criminals. Or, the link will direct you to a Web site that looks and feels like the site you expected — but it’s actually just a front to collect your login information to help the criminals harvest your personal information.
To protect yourself and your users against phishing and pharming schemes, here are four rules to live by:
Criminals have learned that they don’t need to pull a gun on you to get your wallet or purse. They’re using the Internet to steal everything in your accounts — and your good credit too. Take a few simple steps to stop them, and don’t become an identity theft statistic.
Is your organization responsible for complying with one or more of the many privacy-related pieces of legislation that the U.S. government has enacted over the past decade? It’s a good bet that it is.
Whether it’s the Health Insurance Portability and Accountability Act (HIPAA), which addresses healthcare information, the Gramm-Leach-Bliley Act (GLBA), which addresses financial information, or even the Family Educational Rights and Privacy Act (FERPA), which addresses education information, chances are good that one of these affects your organization in some way.
Compliance is nothing to fool around with, and it’s imperative that your organization understand its responsibilities for safeguarding protected data. Protected data is any information that someone could use to identify an individual. Information protected by legislation can include:
Your organization’s network obviously contains and/or processes protected sensitive information. Unauthorized disclosure of such sensitive information could adversely impact your organization with both civil and criminal liabilities. To protect yourself and your company, it’s vital that you implement some extra precautions.
If you’re responsible for the security of your company’s network, then you’re also responsible for overseeing the day-to-day collection, storage, and use of personal data subject to such legislation. You must apply adequate data security safeguards to protect data from the following:
Individuals who fail to follow specific requirements can face fines up to $5,000 per violation, as well as misdemeanor charges. That’s one more reason your organization needs to take appropriate security measures to protect sensitive information. But don’t forget that security measures, no matter how solid, are only as good as the educated employee who wants to do the right thing.
An organization’s users are potentially the weakest link in your security efforts. You’ve heard it before, but it’s worth repeating: Educate your users.
To better protect sensitive data, train all users to do the following:
Privacy-related legislation grew out of a concern over the potential misuse of the vast amounts and types of personal information collected and maintained on corporate networks, which store, manipulate, and transmit the data for a variety of reasons. Don’t become a statistic in the news by mishandling protected information — protect that information with adequate safeguards, and train your users to do the same.
Mike Mullins has served as an assistant network administrator and a network security administrator for the U.S. Secret Service and the Defense Information Systems Agency. He is currently the director of operations for the Southern Theater Network Operations and Security Center.
Today’s Microsoft announcement of moving some R&D from Redmond to a new center in Vancouver, British Columbia heralds the first wave of corporate reaction to the failure of immigration ‘reform.’ The quote from Redmond’s representative is about as subtle as a Pan Galactic Gargle Blaster:
The company said the new location will “allow the company to continue to recruit and retain highly skilled people affected by the immigration issues in the U. S.”
Reinforcement came from Big Blue via the Grey Lady, in which IBM explained to the New York Times they would still need some employees stateside, but moving programming work offshore seems to work just dandy.
Of course, no good deed goes unpunished. Articles have appeared explaining that India information workers are becoming too expensive, with both the Wall Street Journal and Infoworld sending messages just as unsubtle as the Microsoft missive above. Nobody’s jobs are safe if quarterly earnings could be adjusted by a penny, it seems.
Let’s not forget about the genesis of all these stories placed by corporate PR flacks into the MSM. You have seen the video of the attorney explaining how his firm can show Mister Employer how to break immigration law and not get caught, when hiring overseas and avoiding qualified Americans, right? That “A” list material had to, at least in some small way, have been responsible for the Congress’ cooling off on immigration reform, and for scuttling the Real ID provisions buried within it. Thank you, Mister Lawyer; for once, Greed Was Good.
China now allows BlackBerry sales on the Chinese mainland. Research In Motion, the Canadian creators of the BlackBerry, pursued the deal for eight years. Corporate customers in key Chinese cities such as Beijing, Shanghai and Guangzhou will lead the list, and over five thousand are pre-sold.
Chinese language mods for BlackBerries have been in place for over two years in Hong Kong and Macao. Neighbor nations India and Japan already buy BlackBerries, so with CDMA 2000 1X data and GSM 900MHz cellular networks already deployed in China, the market should be well primed. That market’s considerable; there are more Chinese cellphone users then there are people in the United States.
However, China is also developing a homegrown digital system, TD-SCMA, likely with an eye to reaping the benefits of CDMA without paying Qualcomm’s significant royalty fees. New Chinese phones commonly ship with dual-network capability, as this iClone demonstrates.
Where the Chinese market goes, Chinese developers quickly follow, so it seem logical to expect Blackberry clones soon. Nokia already licenses BlackBerry Connect capability in its 9300 and 9300i smartphones.

With comprehensive multi-layer protection, including best-of-breed antivirus, anti-spyware, and the renowned ZoneAlarm firewall, ZoneAlarm Internet Security Suite 7.1 safeguards PC users against today’s most complex online threats. Through its exclusive operating system firewall, ZoneAlarm Internet Security Suite employs the deepest levels of integration with the Vista operating system to proactively prevent threats that basic, traditional firewalls and signature-based systems miss.
Google Hacks is a compact utility that will allow its users to search google using different google search hacks. Using Google Hacks one can easily do a music search by using a highly optimized and complex search command that can be obtained just by clicking a number of option boxes that can be found in the program´s interface.
Click here for Official website.
Click here for Download, size 777kb